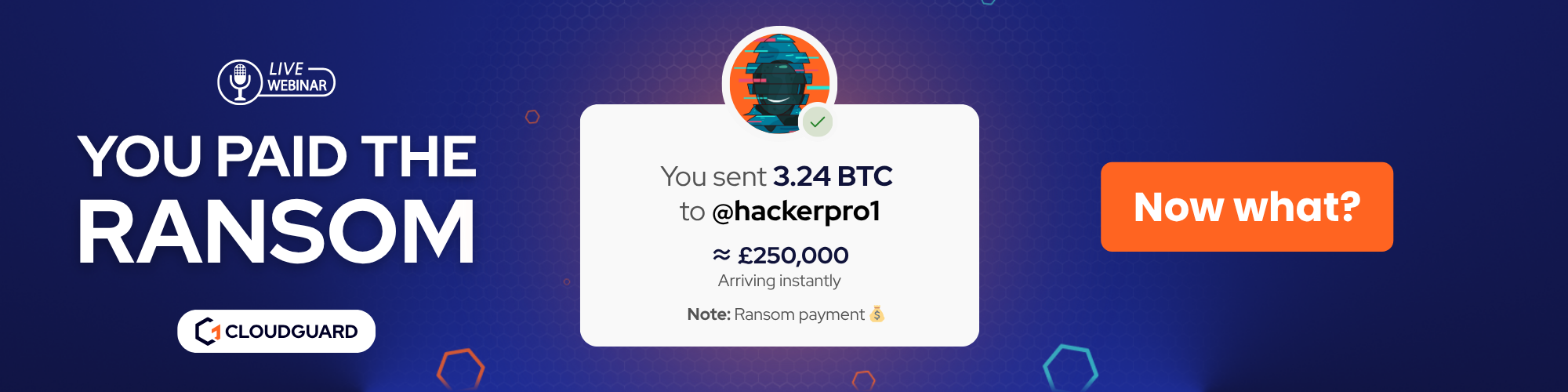
Your company’s been hit by ransomware.
You made the payment.
But nothing’s going according to plan.
What should you have done instead?
Join us for an unfiltered, live incident response simulation that puts you in the war room of a business that just paid the ransom. You’ll make the calls. You’ll feel the pressure. And you’ll see where most IR plans fall apart.
👉 This is not a talk. It’s a test. YOU get to decide the path.
You’ll walk away with real insights into how to lead through chaos, as well as how to build a breach-ready response that actually holds under fire.
You Paid the Ransom: Inside the War Room (Live IR Teardown)
In this webinar, you’ll discover:
We’re not here to theorise. This is a battle-tested, high-impact learning experience with immediate takeaways:
- Experience the first 48 hours after an attack
Get a seat at the decision table during the most critical hours of a ransomware breach. Will you pay the ransom? - Learn to think, not just follow a playbook
Understand the psychology and failure points that cause most IR plans to crumble. - Spot where most teams break. Before yours does
Identify weak points in your own org’s response plan through real-world branching scenarios. - Leave with tools you’ll actually use
Sharpen your leadership, planning and crisis communication capabilities.
This webinar is built from real attack patterns and breach outcomes in the UK.
Who should attend?
- Security leaders (CISOs, CIOs, IR leads)
- Risk and governance professionals
- Business continuity and IT operations heads
- Anyone who owns or influences cyber resilience planning
Why this matters — right now
Ransomware is no longer a matter of if.
The cost of being unprepared? Your data, your uptime, your reputation.
🚨 Loss aversion drives decisions. This simulation will show you exactly what you’re at risk of losing if your IR strategy isn’t built for real-world conditions.