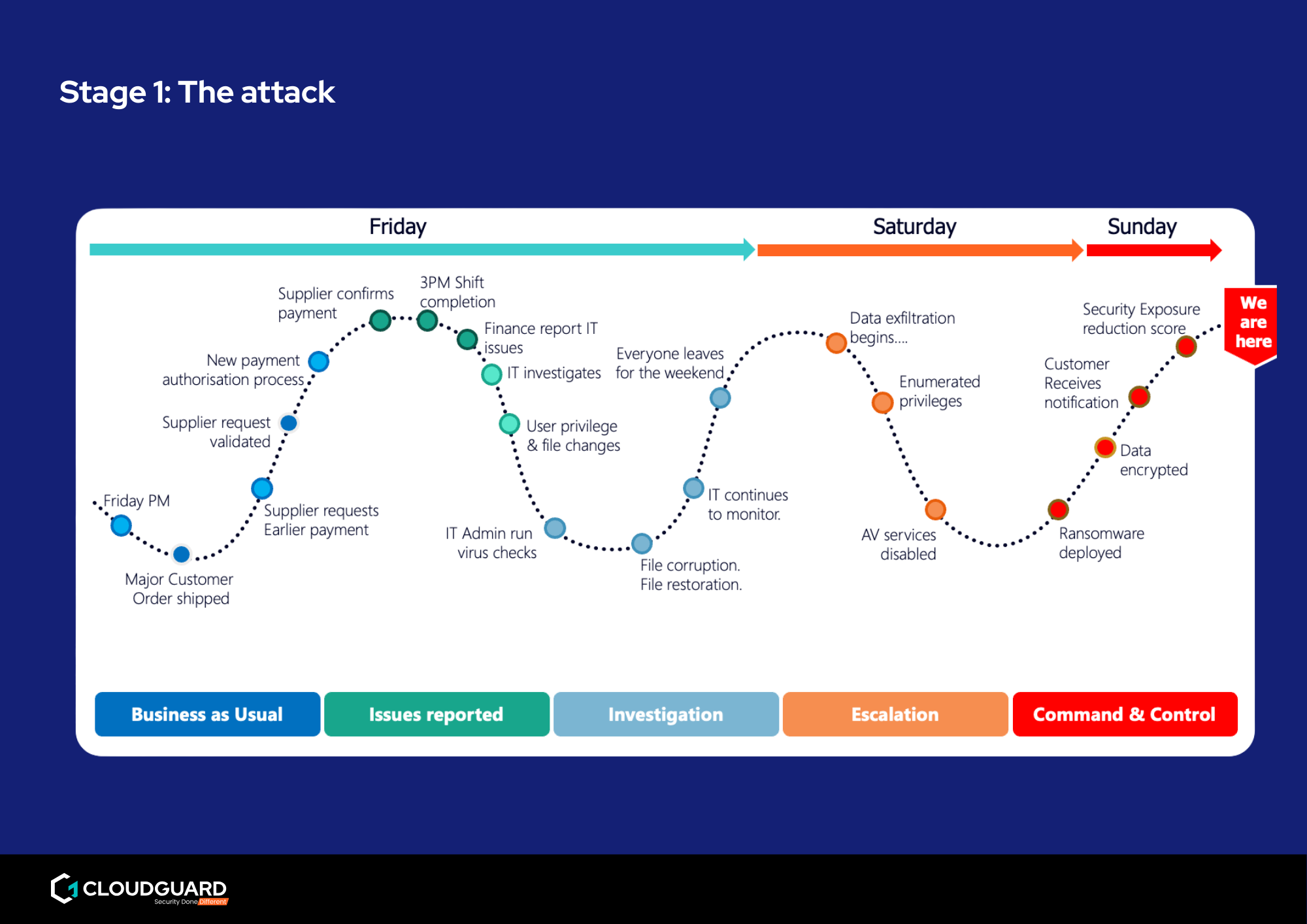
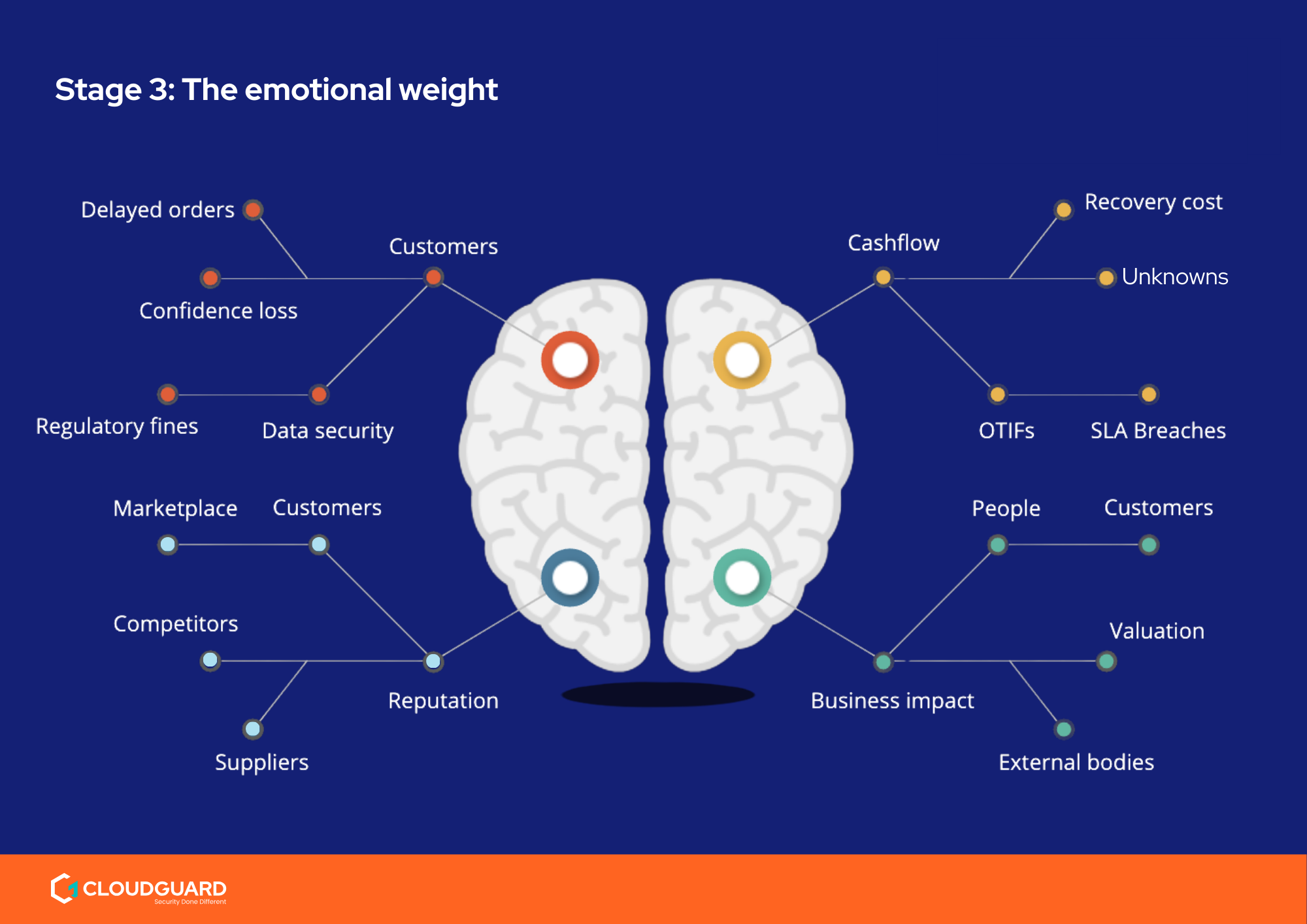
When ransomware hits, the decision whether to pay or not is one of the most intense dilemmas a business leader can face.
We’ve put together a Ransomware Response Guide that takes you behind the scenes of a ransomware crisis inside a UK manufacturing company. With £94M in annual revenue, more than 1,000 customers, and only one IT manager left in place, they suddenly found themselves staring at a £500,000 ransom note with production ground to a halt.
This is a blow-by-blow account of how the attack unfolded, the boardroom conversations that followed and the painful choices made under pressure.
Why This Question Matters
The saying “it’s not a matter of if, but when” is especially true with ransomware.
Even well-run businesses with healthy margins and loyal customers are one attack away from disruption. The guide reveals:
How attackers moved from phishing to full control in just a weekend.
Why production downtime alone was costing the company £225,000 per day.
The legal, financial, and ethical debates that split the board.
The Human Side of Ransomware
Technical damage is only half the story. The other half is the emotional toll.
In the case study, the CEO spent a Sunday morning frantically Googling ransom notes while the board scrambled to understand legal obligations, client communications, and reputational risk. The IT lead admitted: “We had no comms plan. We didn’t know what to tell employees or customers.”
The guide lays bare just how overwhelming the pressure becomes without a pre-defined incident response framework, and why fear and confusion often drive rushed decisions.
The Decision Matrix
Paying the ransom seemed like the fastest path to recovery. But the reality wasn’t so simple. The guide explores both sides:
Not paying: A 10+ day rebuild costing millions in lost business.
Paying: Faster recovery, but no guarantee of data integrity and the risk of secondary extortion.
In the end, the board decided to pay. What followed, though, was far from a clean resolution.
The Aftermath: Lessons Learned
Even after transferring the ransom and receiving a decryptor, the company faced:
Partial recovery that dragged on for weeks.
A second extortion attempt demanding more money.
Customer departures and long-term brand damage.
The guide closes with what the business would do differently, immutable backups, tabletop exercises, breach communications planning, and stronger patch management. These lessons are critical for any organisation that doesn’t want to learn the hard way.
Why You Should Read the Full Guide
This article only scratches the surface. The full Ransomware Response Guide goes deeper into the decision frameworks, cost models, and strategic takeaways every IT and business leader should have ready before they’re in the war room.
👉 [Download the full guide here] to read the full case study and prepare your team for the toughest call they may ever face.