
Over the next few weeks, we plan to publish a series of blog posts exploring cyber security supply chain risk management (C-SCRM) and looking at what you should consider when deciding whether to outsource your C-SCRM programme. We will cover everything from initial explanation of the reasons why you should do it, planning a structured approach, developing and implementing an approach that best suits your company, and how to continually assess and monitor.
These blog posts will give you the experience and knowledge needed to secure your eco-system and help win more business. Check them out as they are released weekly.
In this initial post, we’ll look at C-SCRM is, why it matters, and why you might think about outsourcing it. If you are thinking of outsourcing some, or all, of your C-SCRM programme to an independent or external consultant, there are some things to consider, both beforehand and during the process, to avoid issues arising later.
There is, of course, always the option to manage it yourself, and this series is intended to give you the tools for managing C-SCRM in-house if you prefer.
What is C-SCRM?
Supply chain risks in general are very well understood. For example, your supplier might suffer a disaster, and be unable to supply what you need for your business, so you must find a new supplier. Or there might be a worldwide shortage of a particular product that you need, and nobody else can supply it—or only at great expense.
C-SCRM is more specific: it aims to understand and mitigate the cyber security risks associated with a business’ supply chain, whether this is from the suppliers, their products, or their services, or even their suppliers. C-SCRM involves identifying and assessing the cyber security risk associated with each supplier, determining appropriate mitigating actions for any risks, and then implementing those actions.
Examples of cyber security risks include:
- If your business buys software from a company, and that software contains a security vulnerability that could be exploited by an attacker, your business is at risk of a cyber attack.
- If your business stores data with a third party, and they are attacked, your data may be at risk of being breached.
- If someone working for a supplier (perhaps a systems integrator) with access to your sensitive intellectual property steals it, you could lose your competitive advantage
- If a supplier has access to your IT, they (or an attacker who has gained access to their systems) could damage your systems, data, and reputation.
- If your business depends on a particular widget, but that widget can’t be delivered by your supplier of widgets, because their supplier of widget-parts suffered a ransomware attack, you might have a production issue due to a cyber problem further down the supply chain.
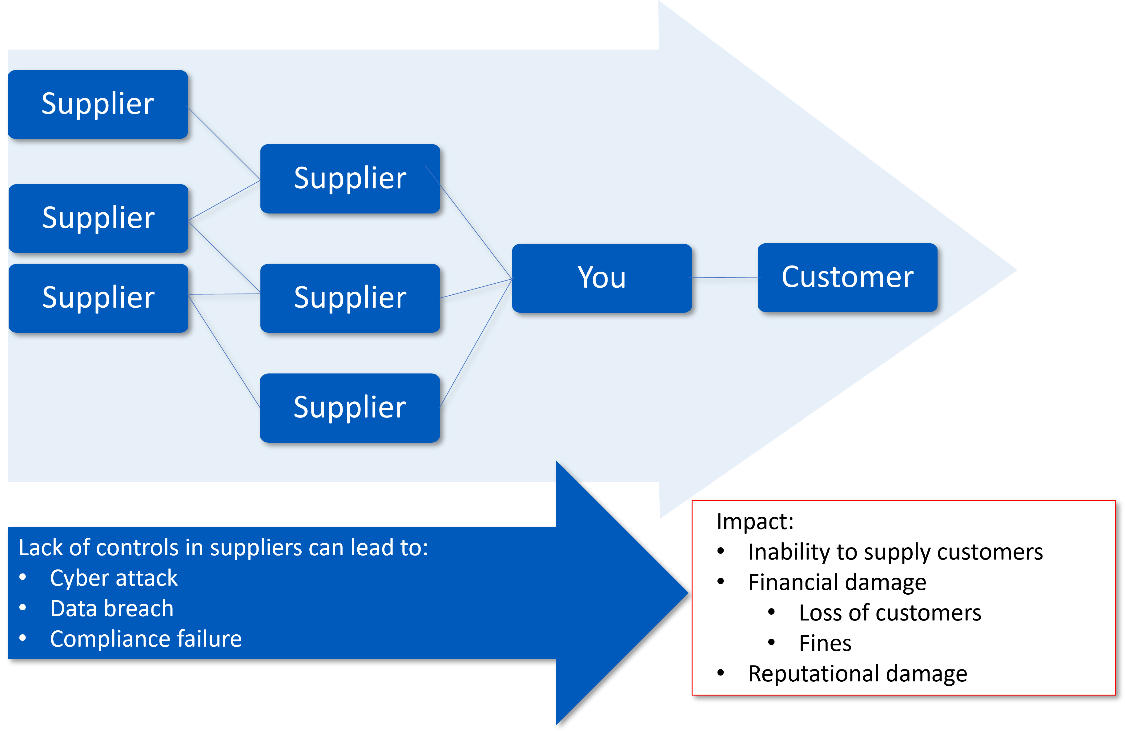
Figure 1: Cyber security supply chain risks
Cyber security supply chain risk management is increasingly seen as an important element of risk management, and so has been added to the draft of NIST Cyber Security Framework v2, within the newly added Govern function. Also, the National Cyber Security Centre has recently created a new collection of resources to support your supply chain security.
Why does it matter?
Why does cyber security supply chain risk management matter?
Cyber criminals are often savvy businesspeople and are likely to target the weakest link in the chain to achieve their goal – which might be to infiltrate your business, or a smaller one that supplies you.
You might deploy significant cost and money on your cyber security technical controls, but cyber criminals will target a smaller, less secure organisation. Why spend millions targeting you when attacks can be generated far more cheaply at your suppliers? Effectively, it is a better return on investment for the business-minded cyber criminals.
By understanding the cyber security precautions your suppliers (and their suppliers in turn) put in place, you can understand where cyber attackers might focus their attention and put in place security controls to minimise the risk to your business and therefore potentially to your customers in turn.
Benefits of C-SCRM
Once you have established a C-SCRM programme, your business will:
- understand which of your critical assets are most susceptible to supply chain weaknesses and vulnerabilities
- reduce the likelihood of supply chain compromise
- have greater assurance that the products you acquire for use in your business are secure
- have greater assurance that suppliers, whether of services or technology, can be relied on to deliver what you need, securely, as required.
This series is intended to help you establish—or strengthen—your C-SCRM programme.
Why outsource?
There are several benefits to hiring an external consultant to carry out some or all of the C-SCRM activities for you. The most relevant benefits in this case include:
- you’ll be able to focus on your core business activities while someone else handles C-SCRM
- you’ll have access to C-SCRM skills and resources that you may not have available for these tasks in your organisation
- and the speed and quality of delivery of these tasks is likely to increase as a result.
You will need to bear in mind, of course, that your consultant will not be an expert in your business and how it operates – you are the expert in that – so will need some time from you and/or your team to cover business-specific areas. You will also need to be honest with them about your business (the issues as well as the successes), so that they can offer the best possible advice for your specific circumstances.
In this series
- On communications, contracts, and meeting expectations
- Planning for success when outsourcing C-SCRM
- Developing a C-SCRM policy and programme
- Assessing current suppliers: where are the security gaps?
- Reviewing current processes: what could we do better?
- Implementing and embedding a C-SCRM programme
About CSP
CSP are a specialist security consultancy helping our clients navigate this increasingly interconnected world. Our team can:
- advise on security requirements, based on your situation
- assess your suppliers against your security requirements at every stage:
- reviewing their responses to security questions
- reviewing security clauses in contracts
- auditing your selected suppliers for compliance with your security requirements.
- work with you to enhance your policies and processes to improve security throughout your procurement process.
Please contact us here or call us on 0113 5323763 to talk about how we can help.









