This article was originally published on 13 January 2023.
You can read the original article on the 6point6 website here.
Cyber security technical debt accrues risk, just as a financial debt accrues interest. 6point6’s Simon Hutchings, Capabilities Director in Cyber Security, and Shruti Kulkarni, Cyber Security Architect, explain what cyber security technical debt is, why it is a problem – and how to address it.
Recognising the importance of cyber security to strengthening and protecting digital public services, the UK Government last year published its National Cyber Strategy 2022. The strategy lays out how the UK intends to develop its cyber power in support of national goals throughout this decade. It highlights the resilience of the country’s digital infrastructure, citing the importance of “preventing and resisting cyber-attacks more effectively” as a key pillar of building a prosperous nation. These objectives are well thought through and aligned to the ambition of strengthening the digital economy, but what could hamper successful execution?
Just like any other organisation, government departments are under constant pressure to deliver new digital services to their citizen customers. This involves building on, consolidating and converging their technological capabilities, as well as modernising complex legacy estates and migrating data.
Through the use of various digital applications and interfaces, these complex legacy systems that power the national infrastructure are increasingly being exposed to different agencies, businesses and public bodies. Hiding here is the nemesis of any IT and Security leader: technical debt, and more specifically, cyber security technical debt!
What is cyber security technical debt?
A Google search will reveal any number of definitions of cyber security technical debt. At 6point6 we define it simply as the gap between the security-assured technology implementation you would have ideally intended – and what is actually operationally live. With systems and architecture becoming ever more complex and interdependent, the debt can also accrue because of refresh cycles, application changes and software upgrades.
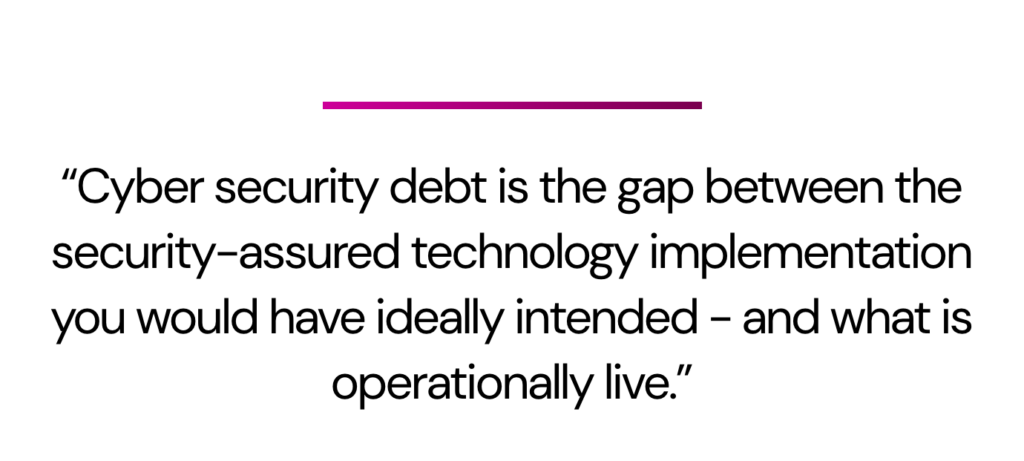
As with financial debt, cyber security technical debt is considered by many organisations to be a necessary evil, taken on in order to accelerate business outcomes. However, this should only be done under specific circumstances and with great care and management. Whilst financial debt comes with interest which can quickly compound, cyber debt brings with it risk which can compound in the same way. The art is in managing the debt and not allowing it to get out of control. It should be paid down carefully and regularly, avoiding a default – or in case of cyber debt, a serious security incident, which will lead to significant reputational damage.
Why is cyber security technical debt a problem?
IT departments across the UK public sector are under constant pressure to deliver new digital services in the shortest possible timeframe. In recent years, stringent external deadlines such as Brexit and the rapid COVID response have pushed the delivery machinery to the brink. In some circumstances the operational urgency to launch services has outweighed the risk of leaving some security aspects unaddressed. In addition, subsequent pressures to improve user experience have further hampered attempts to comprehensively address vulnerabilities.
In the past this might not have been much of a problem with legacy applications and architectures residing behind firewalls and secure perimeters. However, the growth in digital government services, whilst welcomed, can expose potential vulnerabilities to new and wider attack vectors. Risk management alone simply isn’t enough to protect these systems from attack.
The ever-increasing complexity of systems architecture and application interactivity also leads to complications. It is possible that one seemingly insignificant application, hurried through testing to ensure a wider deployment can proceed, could open a back door to systems and infrastructure. This can increase vulnerability to a range of attack vectors, subsequently resulting in outcomes including data loss, ransomware, or virus deployment amongst others. In the case of UK government, the National Cyber Security Centre advises that this can also result in cyber espionage, service disruption or the spread of disinformation.
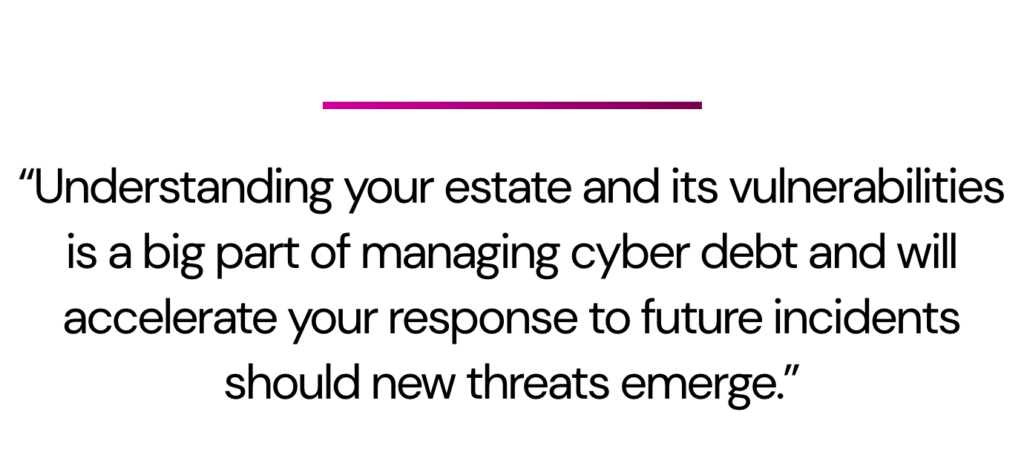
Not dealing with financial debt can result in default. In cyber security terms, not dealing with debt can result in a catastrophic security breach. Quite aside from the obvious risks, the reputational damage resulting from the personal data of millions of citizens ending up in the wrong hands, and the loss of confidence in government that would accompany such an issue would be hugely embarrassing the world over.
Cyber security technical debt can also be introduced when the security processes and controls that have kept the legacy infrastructure working are also used to support the digitisation of services on a restrictive budget. Trying to do more with less has seen many security and IT teams being required to manage ageing infrastructure and add new applications, which bring with them additional complexity. The result is that these same teams no longer have the resources to unpick the cyber security technical debt which has accrued.
In December 2021 a zero-day threat emerged with a 10/10 threat severity score. Many organisations knew that they would be vulnerable because of the Log4j vulnerability, but they simply didn’t know where and how. They lost time responding to the threat, whilst trying to understand their estates and making enquiries of their suppliers and partners.
Planning regular security reviews and holding data centrally on designs, components in use, software composition, patching regimes and support contracts are vital. It’s also important to catalogue software and systems that are out of support or under special or extended support. Some software and code may be irreplaceable and/or unrepairable. In some cases, it may have been around longer than the employees who are expected to look after it. Understanding your estate and its vulnerabilities is a big part of managing it and will accelerate your response to future incidents should new threats emerge.
How should public sector leaders and their IT departments respond to the challenge of cyber security technical debt?
There are four critical areas where public sector leaders and their IT departments should focus their response to the challenge of cyber security technical debt in government. These are:
Engage the organisation
Cyber security technical debt grows over time and when not addressed becomes a “whole of government” challenge to manage. Identifying and assigning a senior executive level sponsor for managing cyber security technical debt is an important first step to creating a joint business and IT collaboration to track and reduce the debt. The aim is to build a culture of awareness around cyber debt so that it becomes the remit of the whole organisation, rather than solely that of the security and IT teams.
It is the role of business leaders to strike the right balance of cyber security and business progress, and all government leaders can have a direct impact on the cyber resilience, safety, and security of the country.Identify and document
Cyber security technical debt must be identified and documented. Some IT teams don’t do this because they regard it as an avoidable or unnecessary cost. Others ignore it as they think it doesn’t provide any tangible user benefit. Understanding the operational implications of a successful breach on the provision of essential services, the fiscal cost of a breach, and recognising the ramifications of reputational impact are the first steps in gaining buy-in to the process of auditing the cyber security debt in any department or organisation. This cataloguing exercise is not a one off but should be conducted on a regular basis.Understand and prioritise
Having gathered and documented your position, it is time to understand it. After running an audit for the first time you may be looking at a report that is daunting in its apparent volume of vulnerabilities. However, not all vulnerabilities are equal. Once you have assimilated the data, you can prioritise and organise your response.Putting your response into action
Whilst understanding the cyber tech debt makes it possible for you to start paying it down, there is also a requirement for constant monitoring and prioritisation to avoid it growing again in future. This is likely to involve buy-in from a number of business and technology stakeholders to ensure security testing and remediation is adopted across all IT implementations. Regular testing in this way will help keep everyone focused on making better security decisions.
How can 6point6 help?
At 6point6 we have an established 5-step approach to support our clients to address cyber security technical debt:
- Conduct an in-depth review and document your current position by gathering and auditing system information through multiple sources
- Understand your risks, both in terms of severity and probability
- Build a balanced and proportionate remediation plan using our architectural approach
- Create stakeholder awareness to prioritise paying down your cyber security technical debt, monitoring and reporting progress
- Further embed security in your IT and Business planning, integrating testing and business need, to help avoid further cyber security technical debt in the future
Getting started
If the price and speed of new digital applications are always the principal motivators, this will lead to the introduction of new cyber debt. It will also result in existing debt being overlooked or parked for resolution in the future.
Whilst complex and changing environments increase the likelihood of cyber debt, they do not make it inevitable. Paying down your debt can start right away. Contact us today to find out more about the proven 6point6 approach to identifying and addressing cyber security technical debt.
ABOUT THE AUTHORS

Simon Hutchings is 6point6’s Capabilities Director in Cyber Security, a role that enables him to combine deep technical understanding with the ability to bridge the gap between business and customers, bringing together all facets of architecture. Shruti Kulkarni is a Cyber Security Architect, harnessing her 15 years’ experience working in Information Security to provide the best security approach that addresses our customers’ unique challenges.